In contrast to Mfkey64, Mfkey32v2 can restore keys without the original tags, which is a significant advantage. This tutorial will cover how to use Mfkey32v2 with PN532Killer on the Windows Program and Android App.
What is Mfkey32v2
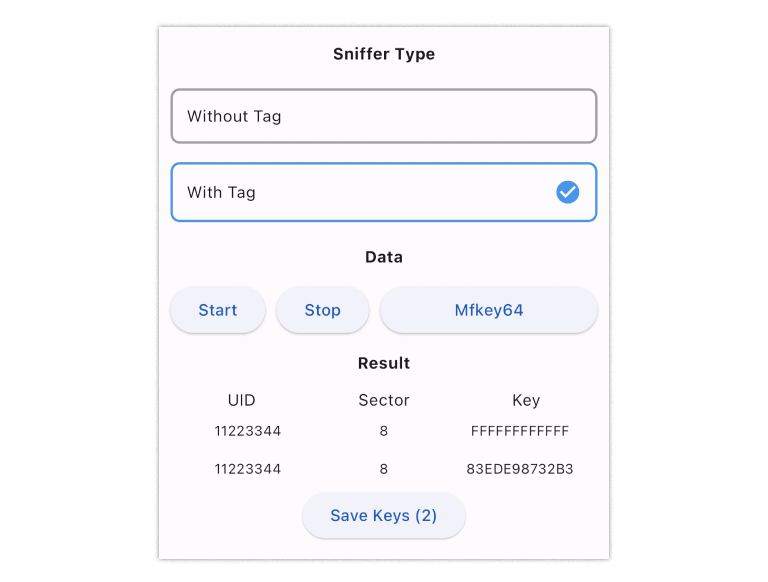
To put it simply, Mfkey32v2 is a tool that helps to generate a Mifare Classic Card’s sector keys. Here’s how it works:
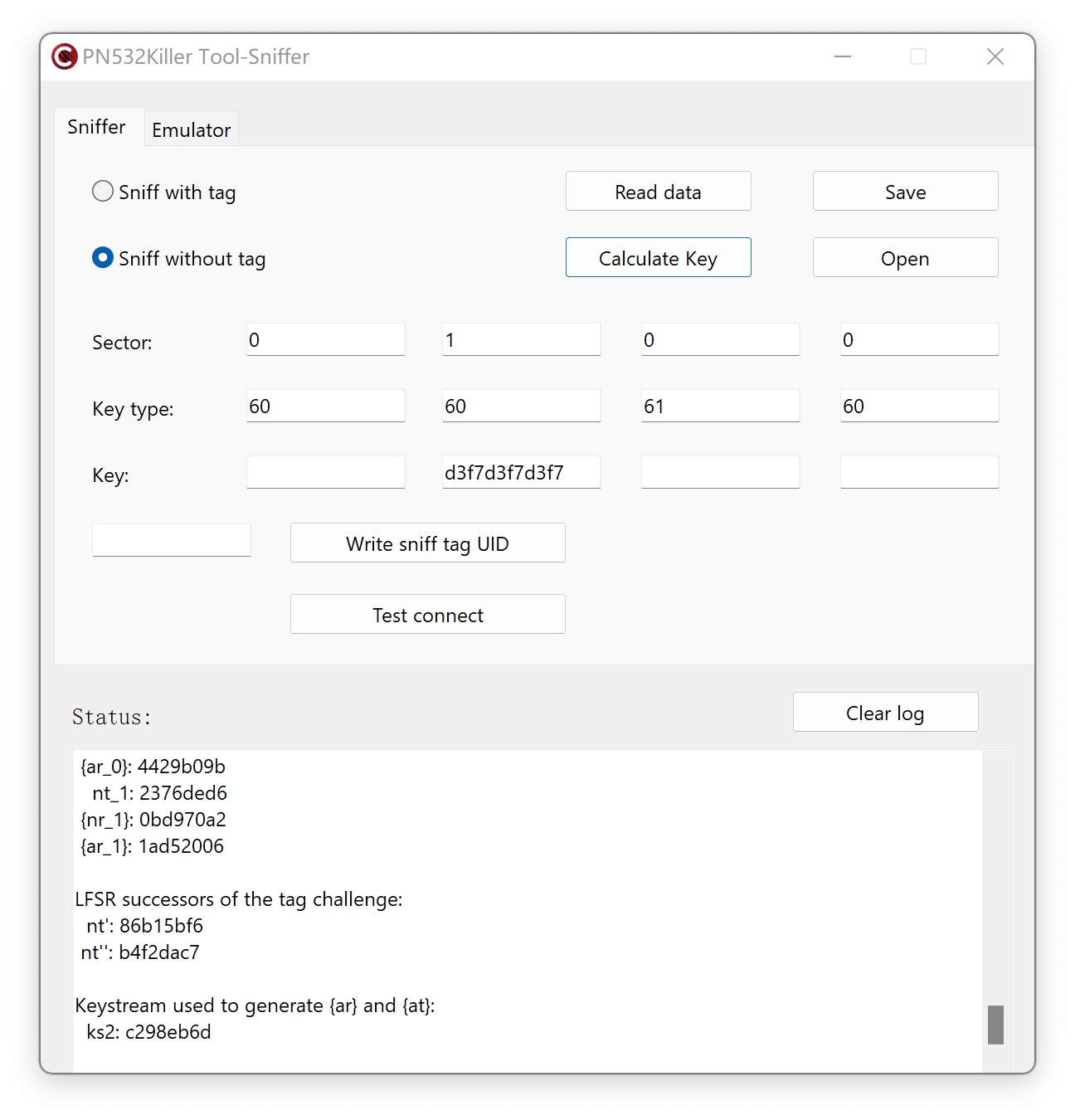
Imagine you have a card and a reader (like a door lock and a key). Now, when the card interacts with the reader, there is a sort of “handshake” or interaction that occurs. The reader sends out what we call “nonces” – these are like secret codes.
Mfkey32v2’s job is to pretend to be the card and collect or record these “nonces” or secret codes sent by the reader. Once Mfkey32v2 has these nonces, it can work its magic and decrypt them or translate them into keys—the ones that are used on the Mifare Classic Card.

Mfkey32 vs Mfkey32v2
• Mfkey32
This is the original program. It needs two consecutive authentication attempts from the same time period. This means, that for it to successfully derive a key, it requires two instances of secret codes (nonces) sent by the reader to the card that occur one after the other without significant delay. It goes like a sequence in a stream.
• Mfkey32v2
Mfkey32v2 is an enhanced version of Mfkey32. Its primary improvement is that the two authentication attempts are not required to occur consecutively or within the same time period. This flexibility makes Mfkey32v2 a significant improvement over the original version as it eliminates the time constraint, thereby increasing efficiency and user friendliness.
Mfkey32 Source Code
- Mfkey32
github.com/Proxmark/…/mfkey32.c - Mfkey32v2
github.com/equipter/mfkey32v2
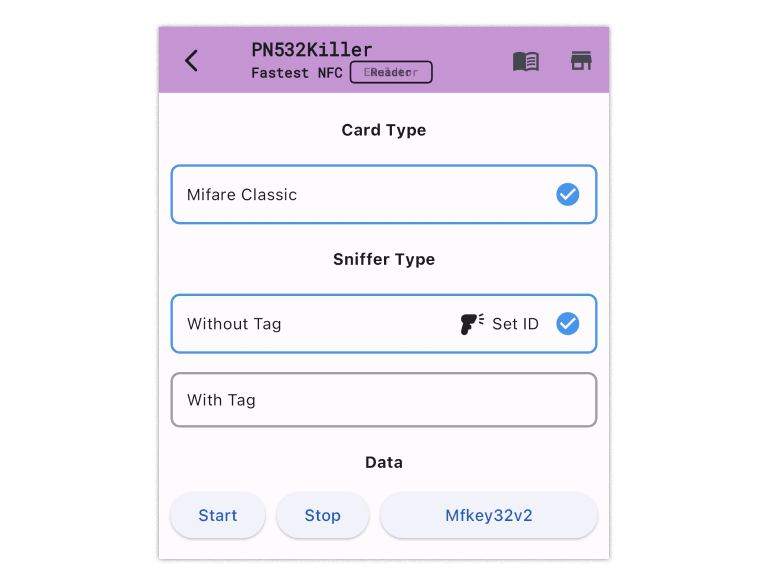
Steps to sniff without tag

Step 1: Enter Sniff14A without Tag

Step 2: Set the UID of the Sniffer slot on the Windows Program or Android App
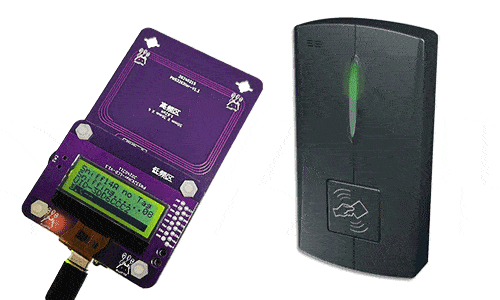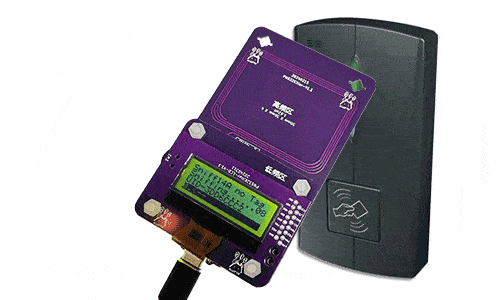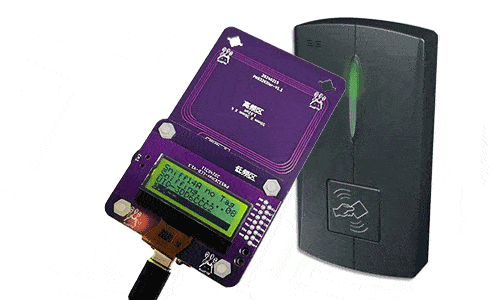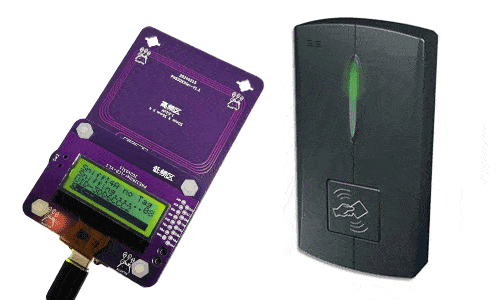
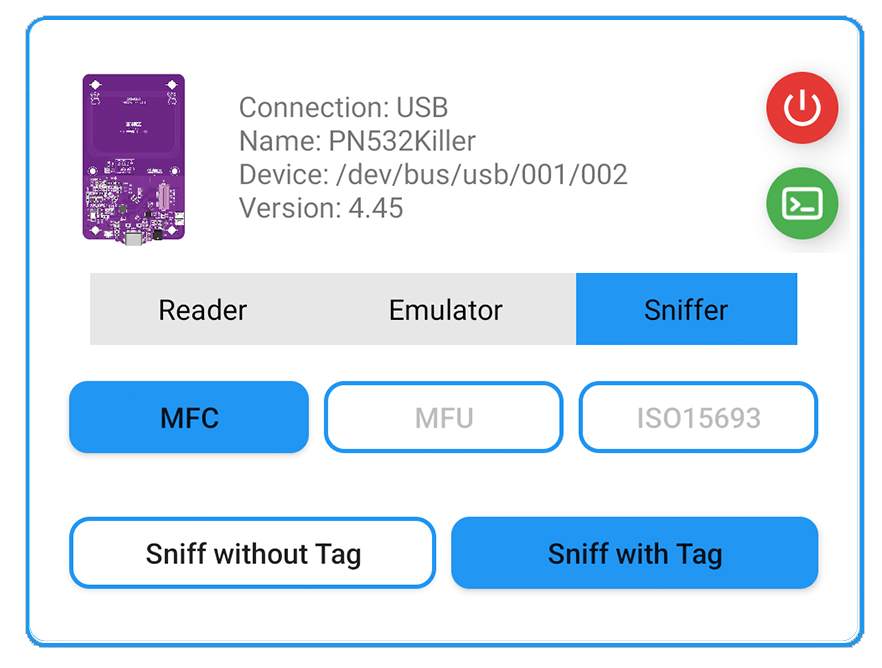
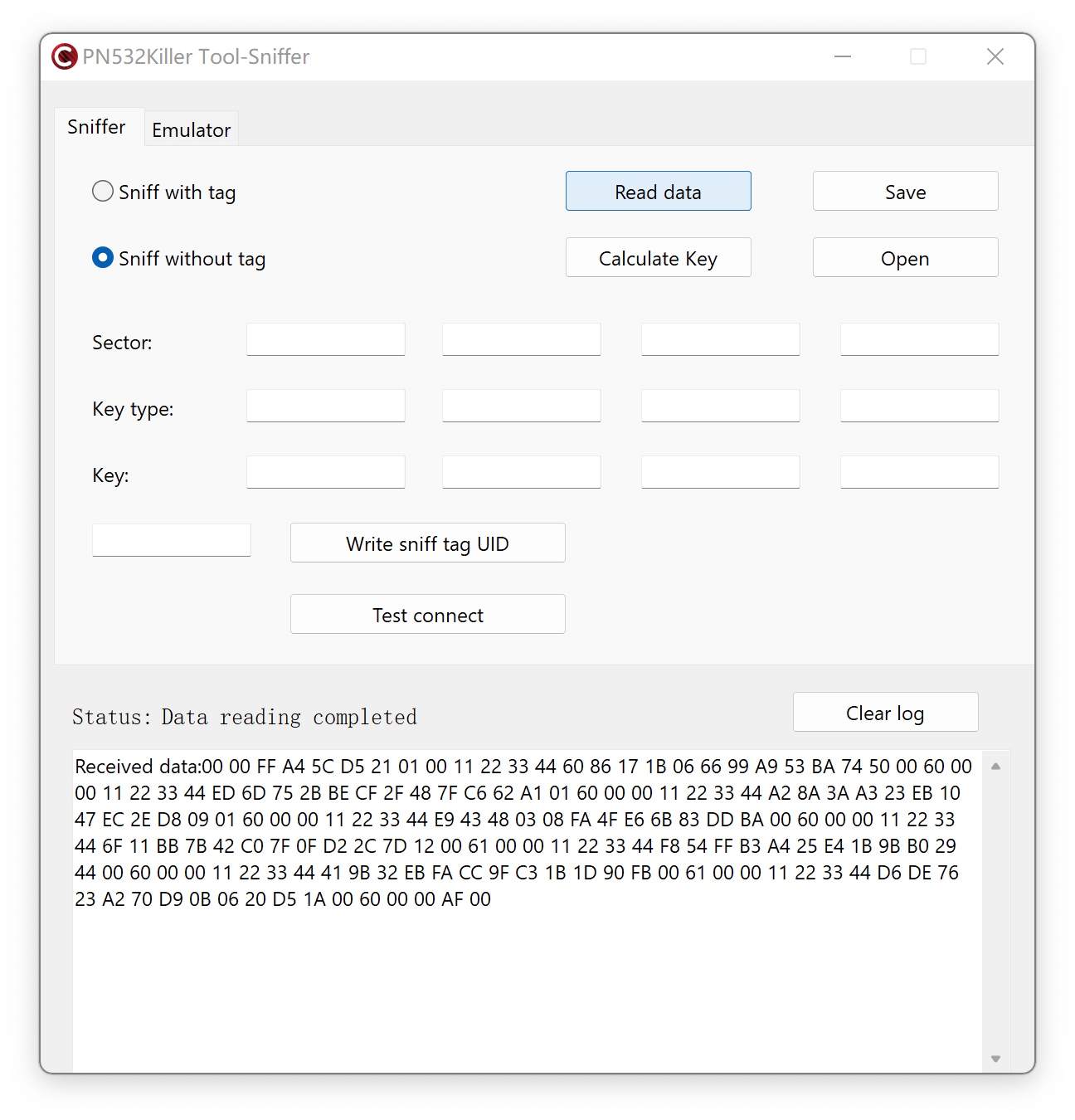
Step 3: Put PN532Killer on the reader over 2 times to get 8 nonces.
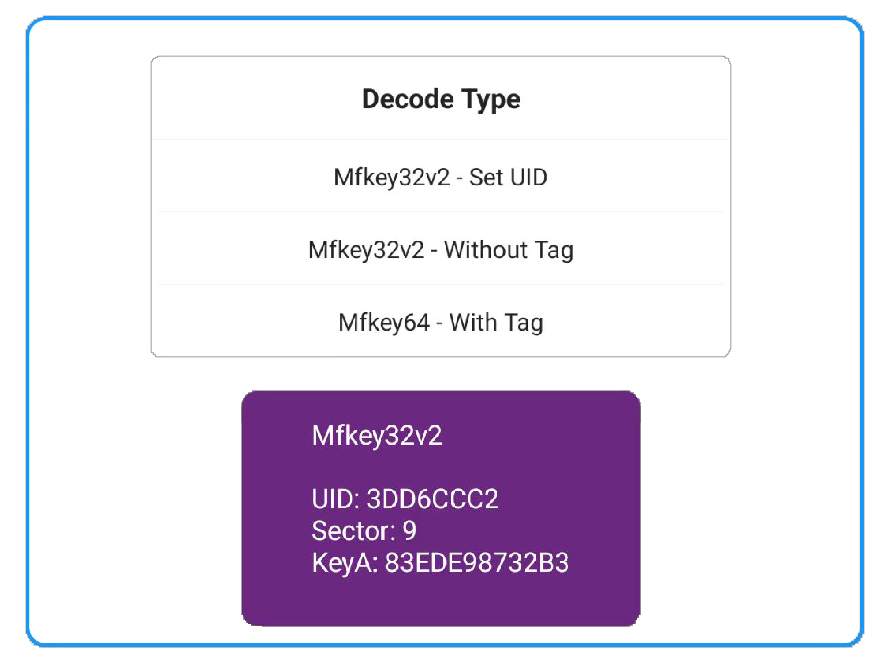

Comments
One response to “How to use Mfkey32v2”
Perfect explanation ✨