Mfkey64 is a powerful tool for analyzing the keys for MIFARE Classic Tags. In this tutorial, we’ll discuss Mfkey64, how it works, its source code, how to retrieve Mfkey64 data using PN532Killer, and how to decode the data on Windows software.
What is MFKey64
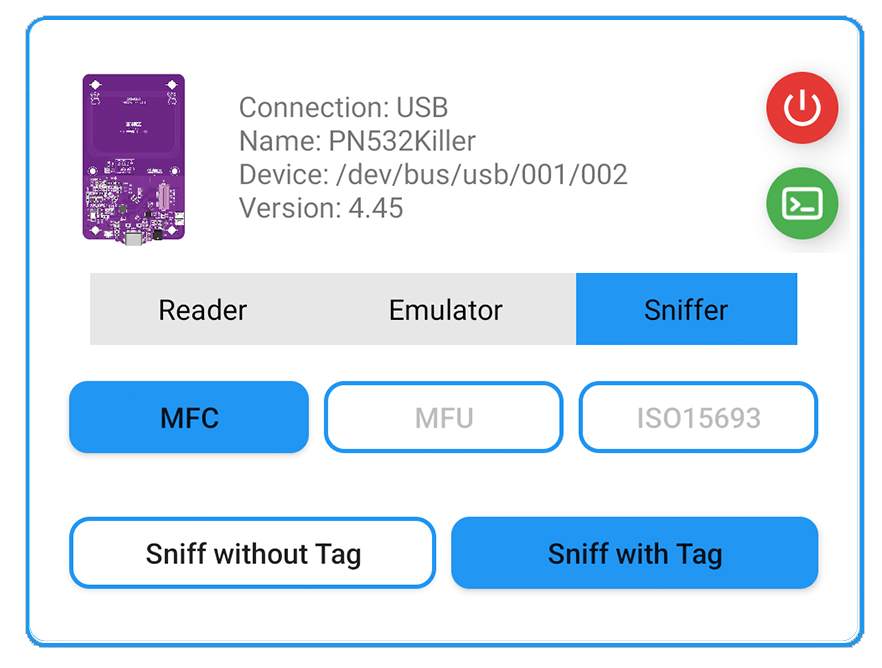
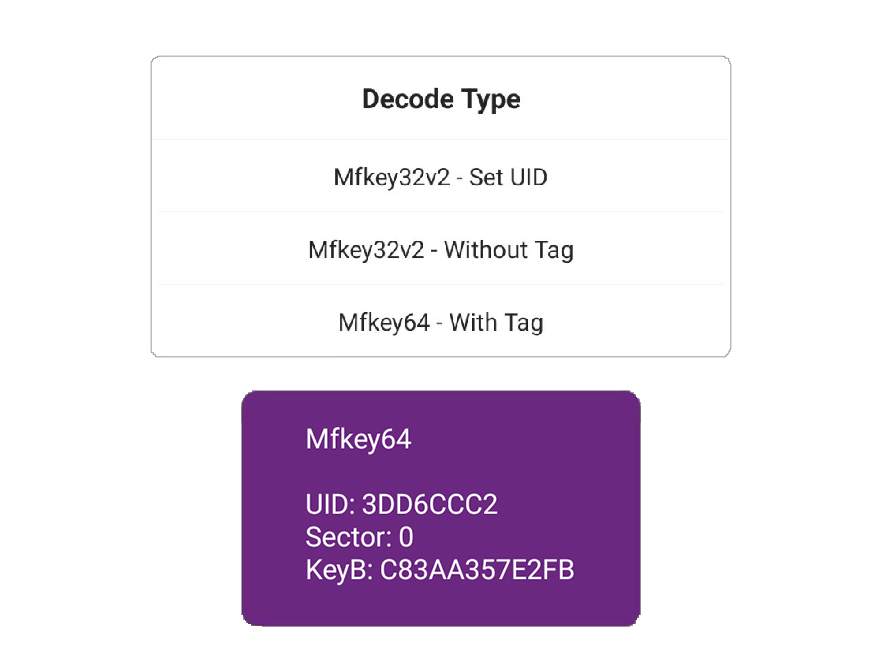
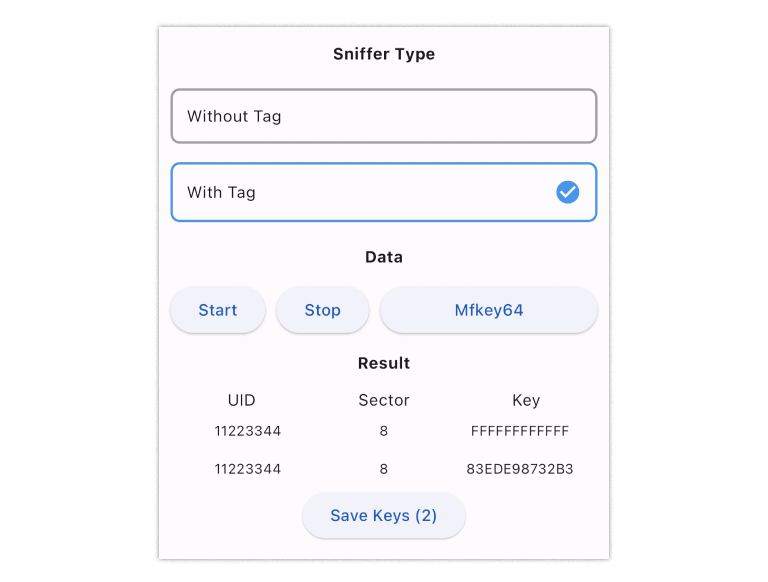
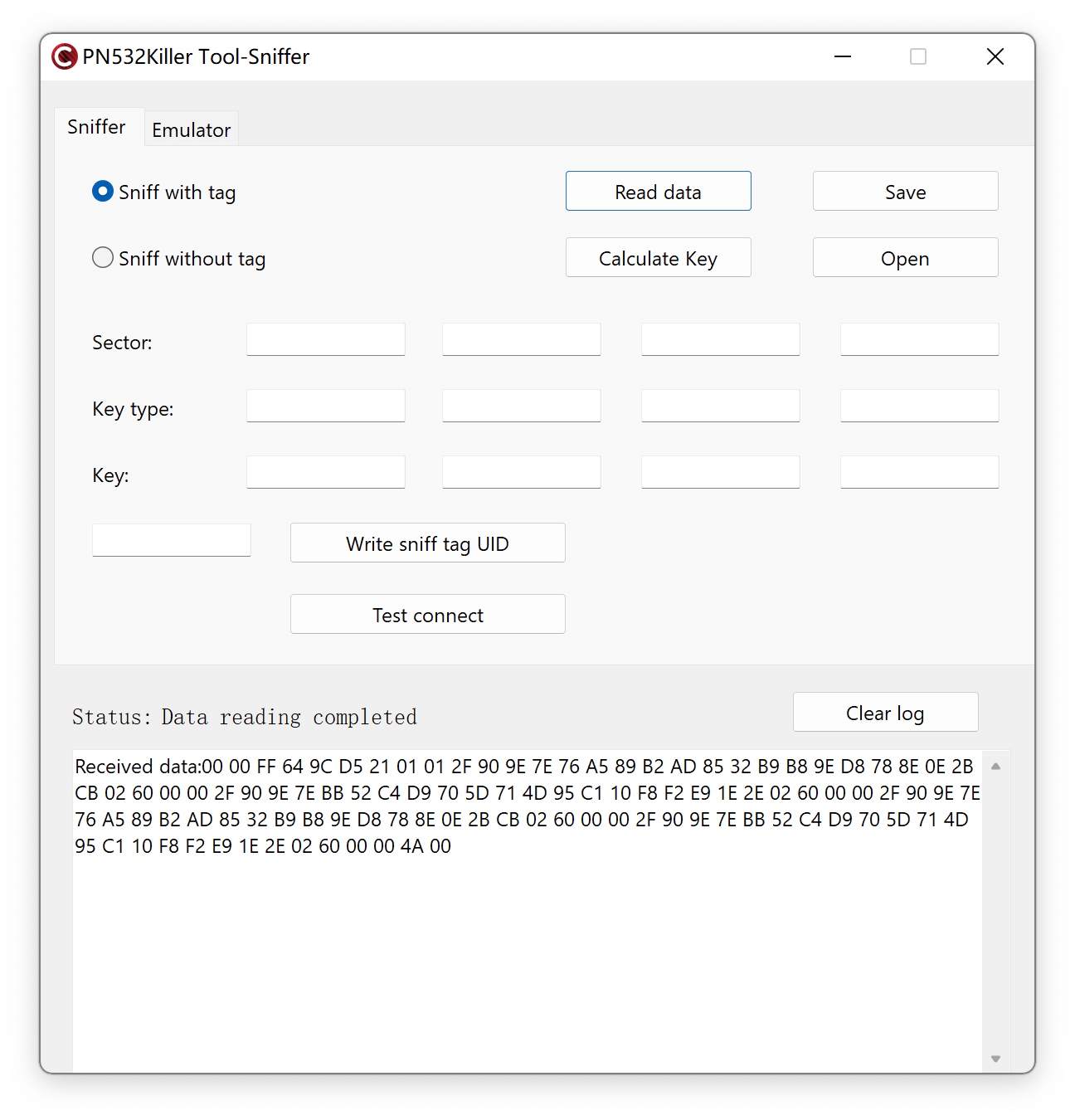
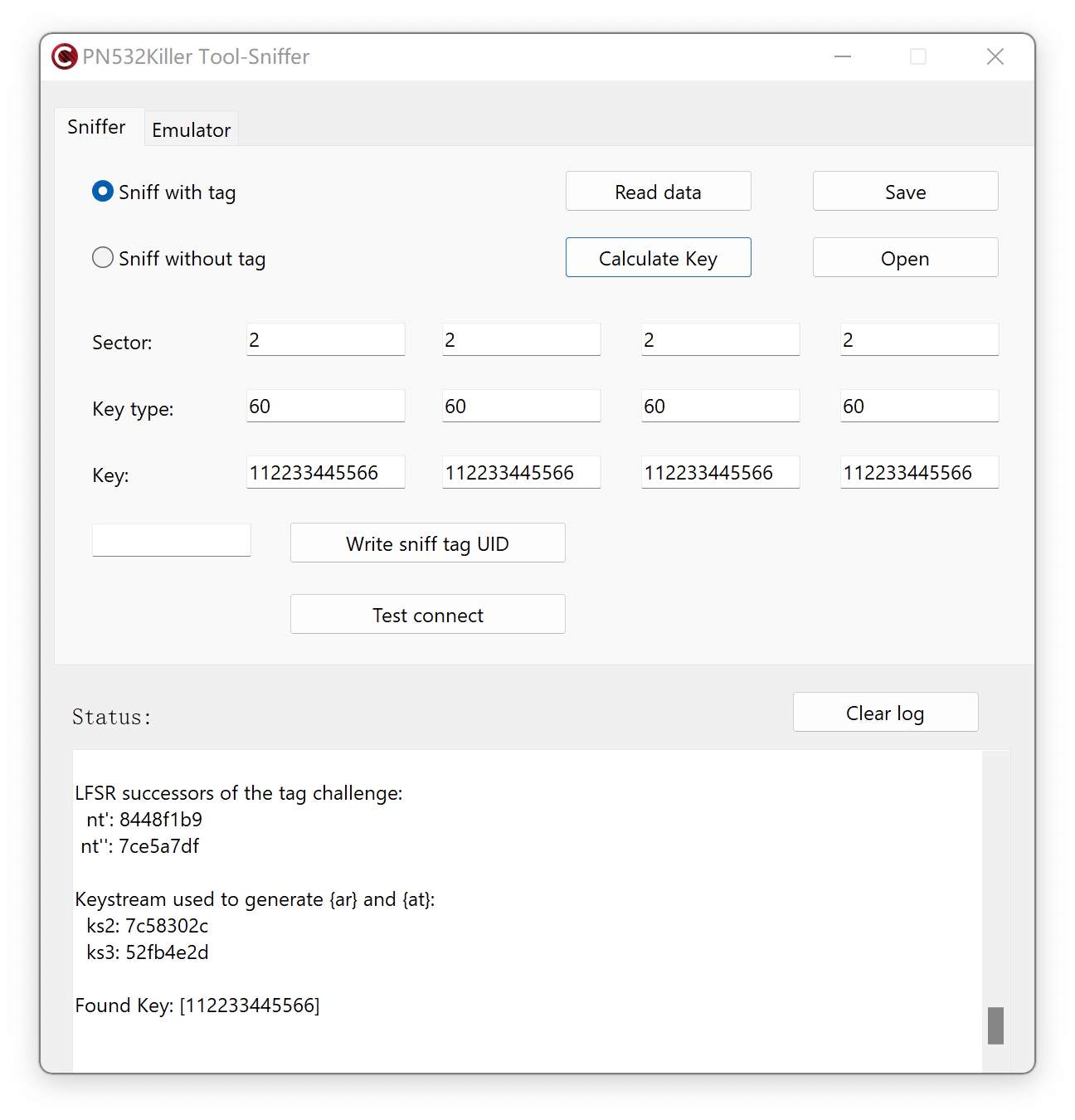
Mfkey64 is an open-source software tool for finding keys to MIFARE Classic Tags. It works on one complete 64-bit keystream authentication between the tag and reader. We also name Mfkey64 as Sniff with tag, which means you must put the PN532Killer and tag together close to the reader while sniffing the authentication logs.
Mfkey64 Source Code
The source code of Mfkey64 comes from the Proxmark3 Repository on Github. It shows the parameters delivered to the function and how it recovers the key from only one complete authentication.1
Video Tutorial
Steps to MFKey64 detection

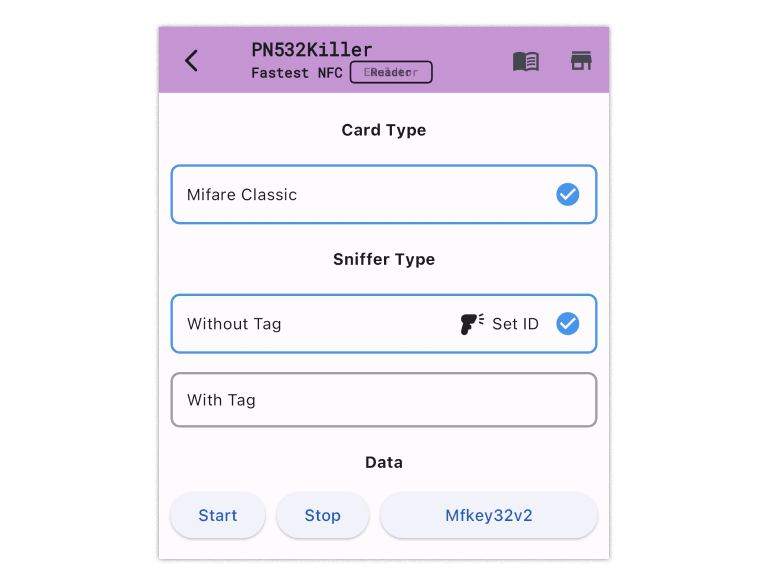
Step 1: Choose Sniff14A with Tag

Step 2: Enter Sniff14A + Tag Mode
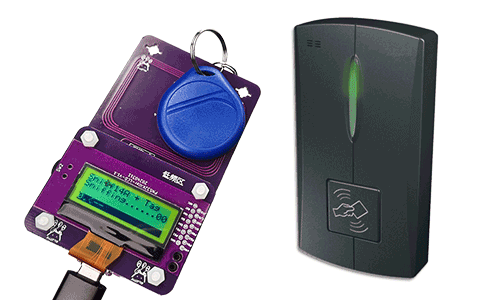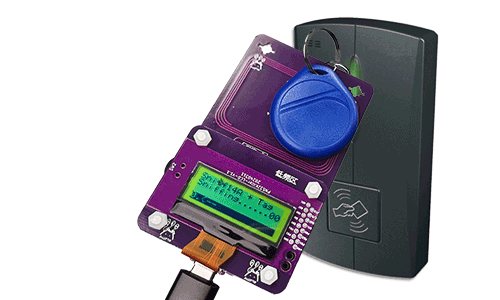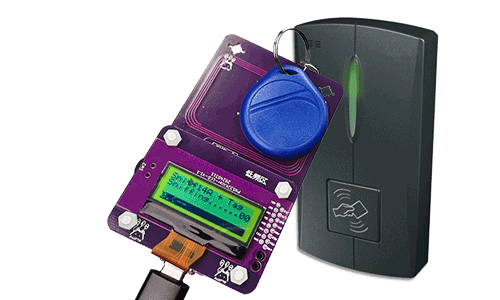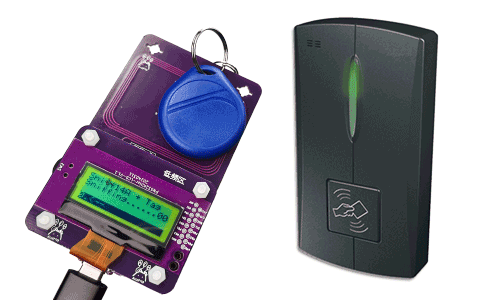
Step 3: Tag & PN532Killer close to the reader.
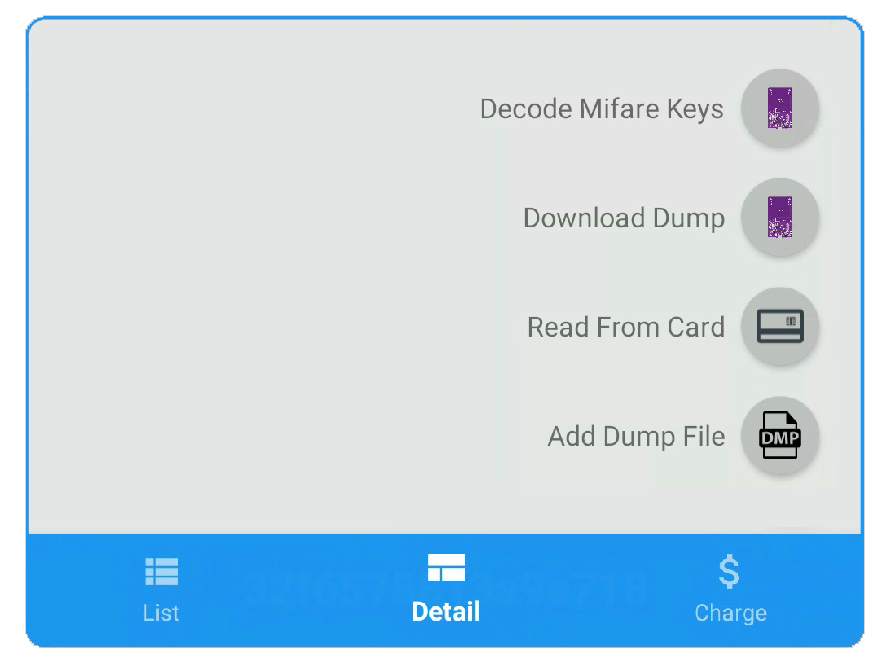
How to check if the MFKey64 logs detected
After several times of sniffing, the number on the screen will turn to 04, which means the Mfkey64 log is sniffed.
Be sure to exit Sniff14A with Tag mode to save the Mfkey64 logs.
Except for text showing on LCD extension, the Red and Green LEDs on the PN532Killer board both will keep on. And you can exit the Sniff14a with Tag mode in the MTools App or MTools BLE App.